Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Parallels RAS allows you to use multi-factor authentication for access control. When multi-factor authentication is used, users will have to authenticate through two successive stages to get the application list. While the first level will always use native authentication (Active Directory / LDAP), the second level can use one of the following solutions:
Azure MFA (RADIUS)
Duo (RADIUS)
FortiAuthenticator (RADIUS)
TekRADIUS
RADIUS
Google Authenticator
Microsoft Authenticator
TOTP (Time-based one-time password)
Multi-factor authentication is more secure because instead of using a standard user name and password, it uses a static user name and a one-time password generated by a token.
Learn how to add an MFA provider in the Adding an MFA provider section.
See also Configuring MFA rules.
The Connection tab lets you specify the following options:
Display name: Specify the name of the OTP connection type that will be displayed on the Logon screen on the client side. This should be the name that your users will clearly understand.
Primary server and Secondary server: These two fields allow you to specify one or two RADIUS servers to include in the configuration. Specifying two servers gives you an option to configure high availability for RADIUS hosts (see below). Specify a server by entering its hostname or IP address or click the [...] button to select a server via Active Directory.
When two RADIUS servers are specified, select one of the following high availability modes from the HA mode drop-down list: Active-active (parallel) means the command is sent to both servers simultaneously, the first to reply will be used; Active-passive (failover) means failover and timeout are doubled, Parallels RAS will wait for both hosts to reply.
HA mode: See Primary server and Secondary server above. If only the Primary server is specified, this field is disabled.
Port: Enter the port number for the RADIUS Server. Click the Default button to use the default value.
Timeout: Specify the packet timeout in seconds.
Retries: Specify the number of retries when attempting to establish a connection.
Secret key: Type the secret key.
Password encoding: Choose from PAP (Password Authentication Protocol) or CHAP (Challenge Handshake Authentication Protocol), according to the setting specified in your RADIUS server.
Click the Check connection button to validate the connection. If the connection is configured correctly, you will see a confirmation message.
Specify additional properties as required:
User Prompt: Specify the text that the user will see when prompted with an OTP dialog.
Forward username only to RADIUS server: Select this option if needed.
Forward the first password to Windows authentication provider: Select this option to avoid a prompt to enter the password twice (RADIUS and Windows AD). Note that for Azure MFA server, this option is always enabled and cannot be turned off.
Please also read a note at the bottom of the dialog (if available) suggesting certain setting specifics for the selected RADIUS solution.
The Automation tab in the RADIUS Properties dialog allows you customize the OTP experience for Parallels Client users by configuring security verification methods and custom commands to be sent to a RADIUS server during the MFA login process. Different security verification methods can be assigned priority and configured to be automatically used.
With this functionality configured, users can choose their preferred security verification method from a predefined and configurable list including Push notification, Phone Callback, SMS, Email, and Custom. The methods appear as clickable icons on the OTP dialog in Parallels Client. When a user clicks an icon, a command is sent to the RADIUS server and the corresponding verification methods is used.
To configure a verification method (also called "actions" here and in the Parallels RAS Console), on the Automation tab, click Tasks > Add. In the Add Action dialog, specify the following properties:
Enable Action: Enables or disables the action.
Title: The text that will appear on the clickable icon in Parallels Client (e.g. "Push").
Command: The OTP command to be used when the action icon is clicked in Parallels Client. Consult your MFA provider for command specifications.
Description: A description that will appear on the user's screen as a balloon when the mouse pointer hovers over the action icon.
Action message: A message to show to the user in the connection progress box.
Select an image: Select an image from the provided gallery. The image is used as the action icon in the OTP dialog in Parallels Client.
When done, click OK to save the action. Repeat the steps above for other actions.
Note: You can create up to five actions. When all five are created, the Tasks > Add menu is disabled.
You can move the actions on the Automation tab up or down the list. This dictates in which order the action icons will be displayed in Parallels Client.
There's one more option that you can configure for an action. It is called Autosend. The option can be enabled for one action only, making it a default action, which will be used automatically without user interaction.
To enable the Autosend option, select an action on the Automation tab and click Tasks > Autosend. To disable the option, click the same menu again. If you enable Autosend for a different action, it will be automatically disabled for the previous action.
There are two possible ways to make an action execute automatically in Parallels Client:
Client is receiving the action icon configuration for the first time and one of the actions has Autosend enabled.
Enabling the Remember last method used option in Policies > Session > Connection > Multifactor authentication. When the option is enabled, and Parallel Client receives the policy, the last method successfully used by the user will become the default automatic method.
When the user logs in to Parallels RAS via MFA, the OTP dialog is shown in Parallels Client with the actions icons positioned above the OTP field. The user clicks an icon and the authentication is carried out according to the predefined action. For example, if the user clicks the "Push" icon, a push notification is sent to the user mobile device where they can simply tap "Approve". Or there could be a "Text me" icon, in which case a text is sent to the user mobile phone with a one-time password. If one of the actions has the Autosend option enabled, then this action is used automatically.
If a user always uses the same authentication method, they can make it the default one. To do so, the user enables the Remember last method used option in the MFA authentication section of the connection properties. Depending on the platform, the option can be found at the following locations:
Parallels Client for Windows / Linux: Connection Advanced Settings > MFA authentication
Parallels Client for Mac: Advanced > MFA authentication
Parallels Client for Chrome: Advanced Settings
Web Client: Settings
Parallels Client for iOS: Connection Settings > MFA authentication
Parallels Client for Android: Settings > MFA authentication
As was already mentioned above, the Remember last method used can also be configured in Client Policies in the RAS Console. The option is enabled by default.
If your RADIUS solution requires configuring attributes, click the Attributes tab and then click Add. In the dialog that opens, choose a desired preconfigured vendor and attribute:
In the Vendor drop-down list, select a vendor.
In the Attribute list, select a vendor attribute.
In the Value field, enter a value for the selected attribute type (numeric, string, IP address, date, etc).
In certain scenarios you may need to add vendors and attributes that are not listed in this dialog. For the information about how to add vendors and attributes, please see the following KB article: https://kb.parallels.com/en/125576.
Click OK and then click OK again .to close all dialogs.
To add an MFA provider:
In the RAS Console, navigate to Connection and select the Multi-Factor authentication tab.
Click Tasks > Add (or click the [+] icon).
Select your MFA provider. A wizard will open.
In the Wizard window, specify the following parameters:
Name: Name of the provider.
Description: Description of the provider.
In the Themes table select the Theme(s) that will use this MFA provider.
Click Next.
Do one of the following:
If you use RADIUS, configure the setting as described in Connection and click Finish.
If you are using a TOTP provider other than Google Authenticator, configure the setting as described in Configuring TOTP.
If you use email to send OTPs, configure the setting as described in Configuring email OTP.
If you use Deepnet DualShield, configure the setting as described in Configuring Parallels RAS to use the DualShield Authentication Platform. For information about configuring DualShield Authentication Platform, see section Configuring DualShield 5.6+ Authentication Platform.
If you use SafeNet, configure the setting as described in Configuring SafeNet.
If you use Google Authenticator, configure the setting as described in Configuring Google Authenticator.
Before reading this section, please read the following important note.
Note: As of July 1, 2019, Microsoft will no longer offer MFA Server for new deployments. New customers who would like to require multi-factor authentication from their users should use cloud-based Azure Multi-Factor Authentication. Existing customers who have activated MFA Server prior to July 1 will be able to download the latest version, future updates, and generate activation credentials as usual: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfaserver-deploy. For new deployments, it is recommended to use Azure NPS Extension https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension or Azure MFA Service along with SAML configuration in RAS.
Depending on the user location, there are four scenarios for the cloud MFA service:
Microsoft Entra ID
Yes
Microsoft Entra ID and on-premises AD using federation with AD FS (is required for SSO)
Yes
Yes
Microsoft Entra ID and on-premises AD using DirSync, Azure AD Sync, Azure AD Connect - no password sync
Yes
Yes
Microsoft Entra ID and on-premises AD using DirSync, Azure AD Sync, Azure AD Connect - with password sync
Yes
On-premises Active Directory
Yes
An Azure account with Global Administrator role is required to download and activate MFA Server. Syncing with Microsoft Entra ID (via AD Connect) or a custom DNS domain aren't required to setup an MFA Server which runs exclusively on-premises.
Users need to be imported into MFA Server and be configured for MFA authentication.
Parallels RAS authenticates users with MFA Server using the RADIUS second level authentication provider. MFA Server thus needs to be configured to allow RADIUS client connections from the RAS server.
The authentication process goes through the following stages:
In stage 2 the user can be authenticated using either RADIUS or Windows AD. A prompt to enter the credentials twice (in stage 1 and 6) is avoided by enabling the option to forward the password.
The below diagram shows the double hop perimeter network scenario with RAS Connection Broker connected to a RADIUS server (RADIUS is located in Intranet but it can be placed in DMZ).
To configure RADIUS properties:
In the Parallels RAS Console, navigate to Connection > Multi-factor authentication.
Double-click the MFA provider that you want to configure.
Read on to learn how to configure RADIUS provider settings.
To configure Google Authenticator settings:
Specify the following:
Display Name: The default name here is Google Authenticator. The name will appear on the registration dialog in Parallels Client in the following sentence, "Install Google Authenticator app on your iOS or Android device". If you change the name, the sentence will contain the name you specify, such as "Install <new-name> app on your iOS or Android device". Technically, you can use any authenticator app (hence the ability to change the name), but at the time of this writing only the Google Authenticator app is officially supported.
User Prompt: Specify the text that the user will see when prompted with an OTP dialog.
The User enrollment section allows you to limit user enrollment via Google Authenticator if needed. You can allow all users to enroll without limitations (the Allow option), allow enrollment until the specified date and time (Allow until), or completely disable enrollment (the Do not allow option). If enrollment is disabled due to expired time frame or because the Do not allow option is selected, a user trying to log in will see an error message saying that enrollment is disabled and advising the user to contact the system administrator. When you restrict or disable enrollment, Google authenticator or other TOTP provider can still be used, but with added security which would not allow further user enrollment. This is a security measure to mitigate users with compromised credentials to enroll in MFA.
Show information to unenrolled users: Select whether unenrolled users can see the The user name or password is incorrect error when they enter incorrect credentials:
Never (most secure): Unenrolled users see a TOTP prompt instead of the error.
If enrollment is allowed: Unenrolled users see the error if user enrollment is allowed. Otherwise, they see a TOTP prompt.
Always: Unenrolled users always see the error.
The Authentication section allows you to configure TOTP tolerance. When using Time-based One-Time Password (TOTP), it is required to have the time synchronized between the RAS Connection Broker and client devices. The synchronization must be performed against a global NTP server (e.g. time.goole.com). Using the TOTP tolerance drop-down list, you can select a time difference that should be tolerated while performing authentication. Expand the drop-down list and select one of the predefined values (number of seconds). Note that changing time tolerance should be used with caution as it has security implications since the time validity of a security token can be increased, thus a wider time window for potential misuse.
Note: When using Time-based One-time Passwords (TOTP) providers, it is required to have both Connection Brokers and client devices time synchronized with a global NTP server (e.g. time.google.com). Adding TOTP tolerance increases the one-time password validity, which might have security implications.
The Reset User(s) field in the User management section is used to reset the token that a user receives when they log in to Parallels RAS for the first time using Google Authenticator. If you reset a user, they'll have to go through the registration procedure again (see Using Google Authenticator in Parallels Client below). You can search for specific users, reset all users, or import the list of users from a CSV file.
Click Finish.
Please also note that the TOTP available time is calculated as the default 30 seconds + x amount of seconds in the past + x amount of second in the future.
Important: To use Google Authenticator or other TOTP provider, the time on a user device must be in sync with the time set on the RAS Connection Broker server. Otherwise, Google authentication will fail.
Google Authenticator is supported in Parallels Client running on all supported platforms, including mobile, desktop, and Web.
To use Google Authenticator, a user needs to install the Authenticator app on their iOS or Android device. Simply visit Google Play or App Store and install the app. Once the Authenticator app is installed, the user is ready to connect to Parallels RAS using two-factor authentication.
To connect to Parallels RAS:
The user opens Parallels Client or Web Client and logs in using his/her credentials.
The multi-factor authentication dialog opens displaying a barcode (also known as QR code) and a secret key.
The user opens the Google Authenticator app on their mobile device:
If this is the first time they use it, they tap Begin and then tap Scan a barcode.
If a user already has another account in Google Authenticator, they tap the plus-sign icon and choose Scan a barcode.
The user then scans the barcode displayed in the Parallels Client login dialog.
If scanning doesn't work for any reason, the user goes back in the app, chooses Enter a provided key and then enters the account name and the key displayed in the Parallels Client login dialog.
The user then taps Add account in the app, which will create an account and display a one time password.
The user goes back to Parallels Client, clicks Next and enters the one time password in the OTP field.
On every subsequent logon, the user will only have to type their credentials (or nothing at all if the Save password options was selected) and enter a one time password obtained from the Google Authenticator app (the app will continually generate a new password). If the RAS administrator resets a user (see the Reset Users(s) field description at the beginning of this section), the user will have to repeat the registration procedure described above.
The Advanced tab lets you specify the error messages sent by the RADIUS server that will not be shown by Parallels Client. This can be useful if an error message is confusing for the user or disrupts user experience.
By default, the "New SMS passcodes sent." is added to the list of ignored messages for DUO Radius. This is done to make authentication via SMS easier for the user. It's not recommended to remove this message from the list of ignored messages.
To add a new message to the list of ignored messages:
On the Advanced tab, Tasks > Add (or click the [+] icon).
Type the exact text of the error message you want to be ignored. Messages are not case sensitive. Please note that you have to specify only the text sent by the RADIUS server. For example, if Parallels Client shows an error that reads "Code [01/00000003] Logon using RADIUS failed. Error: New SMS passcodes sent.", you need to add "New SMS passcodes sent." to the list.
To configure sending OTPs via email:
Configure an SMTP server as described in Configuring SMTP server connection for event notifications.
Specify the following:
Name: The name that will appear in RAS Console.
(Optional) Description: The description of MFA.
Themes: The Themes that use the MFA.
Display name: The name that will appear in Parallels Client.
OTP Lenght: The length of an OTP. Can be between 4 and 20 numbers.
OTP Validity: The time period when an OTP is valid. Can be between 30 and 240 seconds.
User Prompt: Specify the text the user will see when prompted with an OTP dialog.
E-mail subject: The subject of an email containing an OTP.
E-mail content: The content of an email containing an OTP.
Allow users to enroll using external emails: Select this option if you want users to enroll using external email addresses. You can store external emails in RAS Storage or an AD Attribute. If you want to store emails in an Active Directory Custom attribute, you must specify the name of the attribute in the field AD Custom Attribute. You can make sure that you have the permission necessary for storing email addresses in an AD attribute by clicking Validate.
The User enrollment section allows you to limit user enrollment if needed. You can allow all users to enroll without limitations (the Allow option), allow enrollment until the specified date and time (Allow until), or completely disable enrollment (the Do not allow option). If enrollment is disabled due to an expired time frame or because the Do not allow option is selected, a user trying to log in will see an error message saying that enrollment is disabled and advising the user to contact the system administrator. When you restrict or disable enrollment, Google authenticator or other TOTP provider can still be used, but with added security which would not allow further user enrollment. This is a security measure to mitigate users with compromised credentials to enroll in MFA.
Show information to unenrolled users: Select whether unenrolled users can see the The user name or password is incorrect error when they enter incorrect credentials:
Never (most secure): Unenrolled users see a TOTP prompt instead of the error.
If enrollment is allowed: Unenrolled users see the error if user enrollment is allowed. Otherwise, they see a TOTP prompt.
Always: Unenrolled users always see the error.
This section explains how to integrate TOTP MFA providers with Parallels RAS.
For instructions on how to configure Parallels RAS with Duo RADIUS, please read the following Parallels KB article: https://kb.parallels.com/124429.
This section explains how to integrate Deepnet DualShield Authentication Platform 5.6 or higher with Parallels RAS.
You may also read the following documentation on DualShield Authentication Platform:
DualShield Authentication Platform – Installation Guide
DualShield Authentication Platform – Quick Start Guide
DualShield Authentication Platform – Administration Guide
To configure TOTP settings:
Specify the following:
Display Name: The default name here is TOTP. The name will appear on the registration dialog in Parallels Client in the following sentence, "Install TOTP app on your iOS or Android device". If you change the name, the sentence will contain the name you specify, such as "Install <new-name> app on your iOS or Android device".
User Prompt: Specify the text that the user will see when prompted with an OTP dialog.
The User enrollment section allows you to limit user enrollment if needed. You can allow all users to enroll without limitations (the Allow option), allow enrollment until the specified date and time (Allow until), or completely disable enrollment (the Do not allow option). If enrollment is disabled due to expired time frame or because the Do not allow option is selected, a user trying to log in will see an error message saying that enrollment is disabled and advising the user to contact the system administrator. When you restrict or disable enrollment, Google authenticator or other TOTP provider can still be used, but with added security which would not allow further user enrollment. This is a security measure to mitigate users with compromised credentials to enroll in MFA.
Show information to unenrolled users: Select whether unenrolled users can see the The user name or password is incorrect error when they enter incorrect credentials:
Never (most secure): Unenrolled users see a TOTP prompt instead of the error.
If enrollment is allowed: Unenrolled users see the error if user enrollment is allowed. Otherwise, they see a TOTP prompt.
Always: Unenrolled users always see the error.
The Authentication section allows you to configure TOTP tolerance. When using Time-based One-Time Password (TOTP), it is required to have the time synchronized between the RAS Connection Broker and client devices. The synchronization must be performed against a global NTP server (e.g. time.goole.com). Using the TOTP tolerance drop-down list, you can select a time difference that should be tolerated while performing authentication. Expand the drop-down list and select one of the predefined values (number of seconds). Note that changing time tolerance should be used with caution as it has security implications since the time validity of a security token can be increased, thus a wider time window for potential misuse. Note: When using TOTP providers, it is required to have both Connection Brokers and client devices time synchronized with a global NTP server (e.g. time.google.com). Adding TOTP tolerance increases the one-time password validity, which might have security implications.
The Reset User(s) field in the User management section is used to reset the token that a user receives when they log in to Parallels RAS for the first time using the TOTP provider. If you reset a user, they'll have to go through the registration procedure again (for instruction on doing this for Google Authenticator, see Using Google Authenticator in Parallels Client). You can search for specific users, reset all users, or import the list of users from a CSV file.
Click Finish.
Please also note that the TOTP available time is calculated as the default 30 seconds + x amount of seconds in the past + x amount of seconds in the future.
Once DualShield has been enabled the users will have two-factor authentication. If using software tokens such as QuickID the administrator does not have to create a token for each user. RAS Connection Broker will automatically create the token when the user tries to log in for the first time.
When a user tries to access a RAS Connection from Parallels Client, they are first prompted for the Windows username and password. If the credentials are accepted, RAS Connection Broker will communicate with the DualShield server to create a unique token for that user.
If using MobileID or QuickID, an email about where to download the appropriate software will be sent to the user.
If using QuickID tokens, the application will ask for a One-Time Password which is sent by e-mail or SMS.
When asked for OTP, enter the One-Time Password to log in to the Parallels ApplicationServer XG Gateway.

To configure Deepnet DualShield settings:
Specify the following:
Server: Hostname of the Deepnet server.
Enable SSL: Whether to use SSL when connecting to the Deepnet server.
Port: Port used for connection to the Deepnet server.
Agent: Agent name that will be used during registration.
Click the Check Connection button to test that the authentication server can be reached and to verify that the RAS Console is registered as a DualShield agent. If you see the "DeepNet server not valid" message, it could be dues to the following:
The specified server information is incorrect
You need ot allow auto registration of the Parallels components as a DualShield agent.
If you need to allow auto registration of the Parallels components as a DualShield agent, do the following:
Go back to the DualShield Management Console and select Agents from the Authentication menu as shown below.
Select Auto Registration.
Select the Enabled option and set the date range.
Once the Agent Auto Registration is set, go back to the RAS Console and select Yes. You should see a message that the Dual Shield agent has been successfully registered.
Please note that all RAS Connection Brokers must be registered with Deepnet DualShield server. If you are using secondary Connection Brokers, you need to close all open windows until you can press Apply in the RAS Console. This will inform all the agents to self-register as DualShield agents.
Go back to the RAS Console and click Next.
Specify the following:
Application: Name of the Application created in Configuring DualShield 5.6+ Authentication Platform.
Default domain: Domain that will be used if the domain was not specified by the user, in the Theme properties or in the Connection settings.
In the Mode drop-down list, and select how you want your users to be authenticated:
Mandatory for all users means that every user using the system must log in using two-factor authentication.
Create token for Domain Authenticated Users will allow Parallels RAS to automatically create software tokens for Domain Authenticated Users. Choose a token type from the drop-down list. Note that this option only works with software tokens, such as QuickID and MobileID
Use only for users with a DualShield account will allow users that do not have a DualShield account to use the system without have to login using two-factor authentication.
In the Allow channels section, select the channels that will be used to send OTPs to users.
Click Finish.
The following is the list tokens supported by Parallels RAS:
MobileID (FlashID is not integrated with MobileID)
QuickID
GridID
SafeID
SecureID (RSA)
DigiPass (Vasco)
If using hardware tokens such as SafeID the token information must first the XML file provided. Click on ‘Import’ and browse for the XML file provided. After the XML file has been imported each hardware token must be assigned to a user.
SafeNet Token Management System provides a high-value of protection via secure tokens which makes it a perfect tool for second-level authentication in Parallels RAS.
To configure SafeNet settings:
In the Connection section, enter the valid URL into the OTP Service URL field. To verify that the connection with the OTP Service can be established, click the Check connection button.
Note: RAS Connection Broker communicates with the SafeNet Token Management System Server. It is highly recommended to have this behind a firewall for security reasons.
Click the Authentication tab.
In the Mode drop-down list, select how you want your users to be authenticated.
The available modes are:
Mandatory for all users: every user using the system must login using two-factor authentication.
Create token for Domain Authenticated Users: Allows Parallels RAS to automatically create software tokens for Domain Authenticated Users. Choose a token type from the drop-down list. Note that this option only works with software tokens.
Use only for users with a SafeNet account: Allows users that do not have a SafeNet account to use the system without having to login using two-factor authentication.
In the TMS Web API URL field, enter the location of the SafeNet API URL.
In the User Repository field, enter the user repository destination.
Click Finish.
In Parallels Client — New Account Info dialog:
Enter any four digits in the OTP PIN number field (these digits will be required further on in the process).
Enter your email address and then click on OK.
Log into your email account and retrieve the email containing the information you will need to activate your SafeNet authentication. An example of this email is shown below.
Activation Key: YZQHoczZWw3cBCNo
Token Serial: 4F214C507612A26A
Download MobilePASS client from: http://localhost:80/TMSService/ClientDownload/MobilePASSWin.exe
*Login with domain credentials.
*Place the attached seed file in the same folder as the MobilePASS client.
Enter the One-Time Password to log into the RD Session Host Connection.
Application PIN: 4089
Download the MobilePASS client from the URL provided in the email.
Enter the Activation Key found in the SafeNet email.
Next, input the application PIN found in the email into the MobilePASS PIN field.
Click Generate to generate the eToken number and then click Copy.
Combine the OTP PIN and eToken in this order: OTP + eToken.
Enter this value into the Parallels Client and click OK to log in.
After following all the specified steps in "DualShield Authentication Platform – installation Guide" a URP is automatically opened in your internet browser (http:// LOCALHOST:8073) which allows you to logon to the Management Console of DualShield.
Login in to the DualShield Management Console with the default credentials (User: sa, Password: sa). You will be prompted to change the default password.
Applications are set to provide a connection to realm, as the realm contains domains of users who will be allowed the access to the application.
Realm is set for multiple domain users to be able to access the same application.
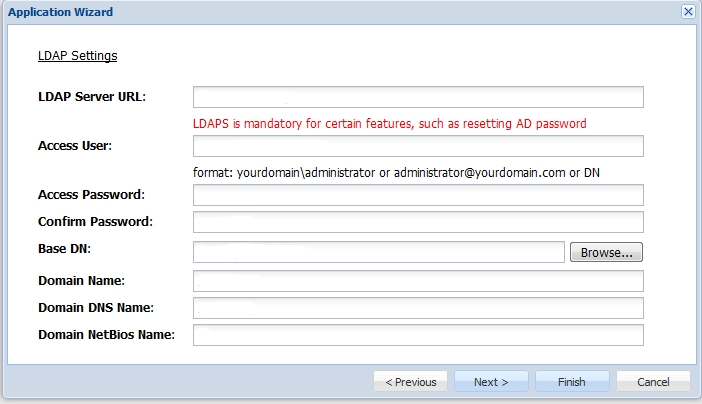
You need to create an Application which Parallels RAS will communicate with. Click on Authentication > Application Wizard and enter the information shown below and press Next.
Specify the LDAP Server settings as shown below and press Finish.
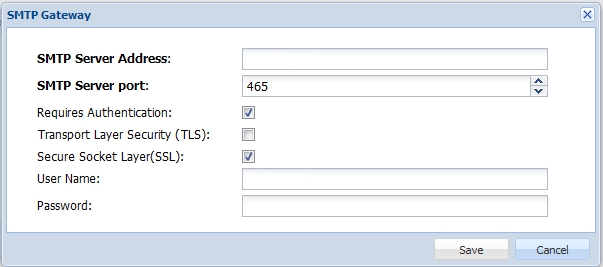
After you have configured the application you need to configure an Email or SMS gateway which are used by DualShield server to communicate with the end user. In this document we will be using an Email gateway. Select Gateways from the Configuration menu.
Configure your email gateway.
Click Edit to enter your SMTP server information
Multi-factor authentication (MFA) can be enabled or disabled for all user connections, but you can configure more complex rules for specific connections. This functionality allows you to enable or disable MFA for the same user, depending on where the user is connecting from and from which device. Each MFA provider has one rule that consists of one or several criteria for matching against user connections. In turn, each criteria consists of one or several specific objects that can be matched.
You can match the following objects:
User, a group the user belongs to, or the computer the user connects from.
Secure Gateway the user connects to.
Client device name.
Client device operating system.
IP address.
Hardware ID. The format of a hardware ID depends on the operating system of the client.
Notice the following about the rules:
Criteria and objects are connected by the OR operator. For example, if a rule has a criteria that matches certain IP addresses and a criteria that matches client device operating systems, the rule will be applied when a user connection matches one of the IP addresses OR one of the client operating systems.
To configure a rule:
In the RAS Console, navigate to Connection and select the Multi-Factor authentication tab.
Double-click on the provider you want to create the rule for.
Select the Restrictions tab.
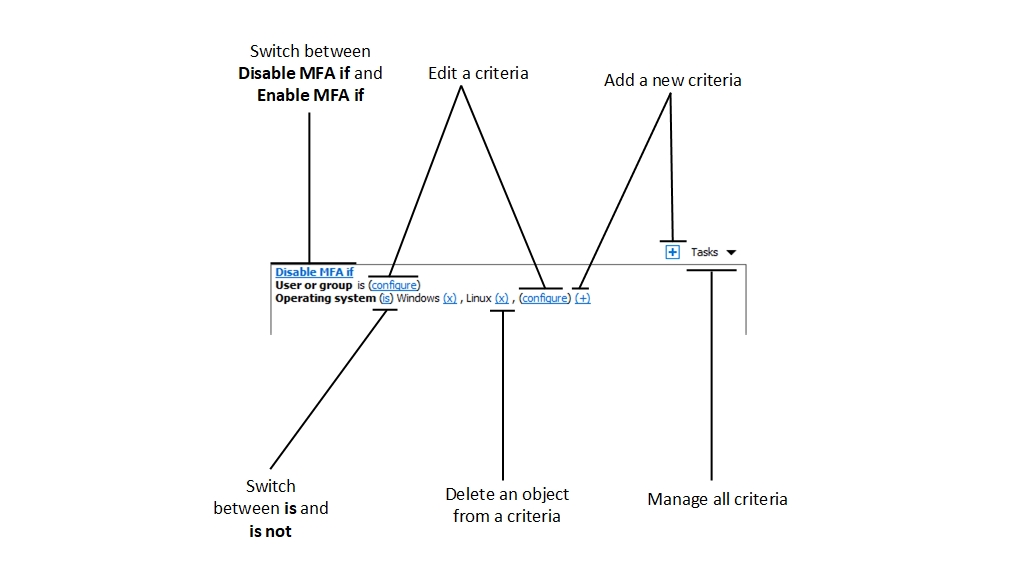
Specify criteria for the rule. You will find the following controls:
Enable MFA if and Disable MFA if: specifies whether the MFA provider must be enabled when a user connection matches all the criteria. Click on the link to switch between the two options.
(+): adds a new criteria. If you want to match a Secure Gateway, a client device name, a client device operating system, an IP address or a hardware ID, click (+). In the context menu that appears, select the type of an object that you want to match and add the specific objects in the dialog that appears. The new criteria appears on the next line.
(X): Deletes a specific object from matching. For example, you want to delete IP address 198.51.100.1 from matching, click (X) next to it. This control appears when at least one object is added. If all objects in a criteria are deleted, the criteria is removed.
is and is not: specifies whether the MFA provider must be enabled when a user connection matches the criteria. Click on the link to switch between the two options. This control appears when at least one object is added.
configure: edits the list of objects to be matched. Click this link to add or delete new objects. Note that for the first criteria (User or group) this link is called everyone. It will change to configure once you specify objects for this criteria.