Single-hop DMZ (two firewalls)
In a single-hop DMZ scenario, the firewall system must be capable of routing connections properly from RAS Secure Gateways to RAS Connection Brokers. The firewall system is also responsible for connections from the Internet to the virtual IP address of a HALB Virtual Server (HALB VS) representing HALB virtual appliance(s) or other generic protocol load balancing scenarios. Note that in this case two HALB Virtual Servers are used for internal and external traffic load balancing to internal Secure Gateways.
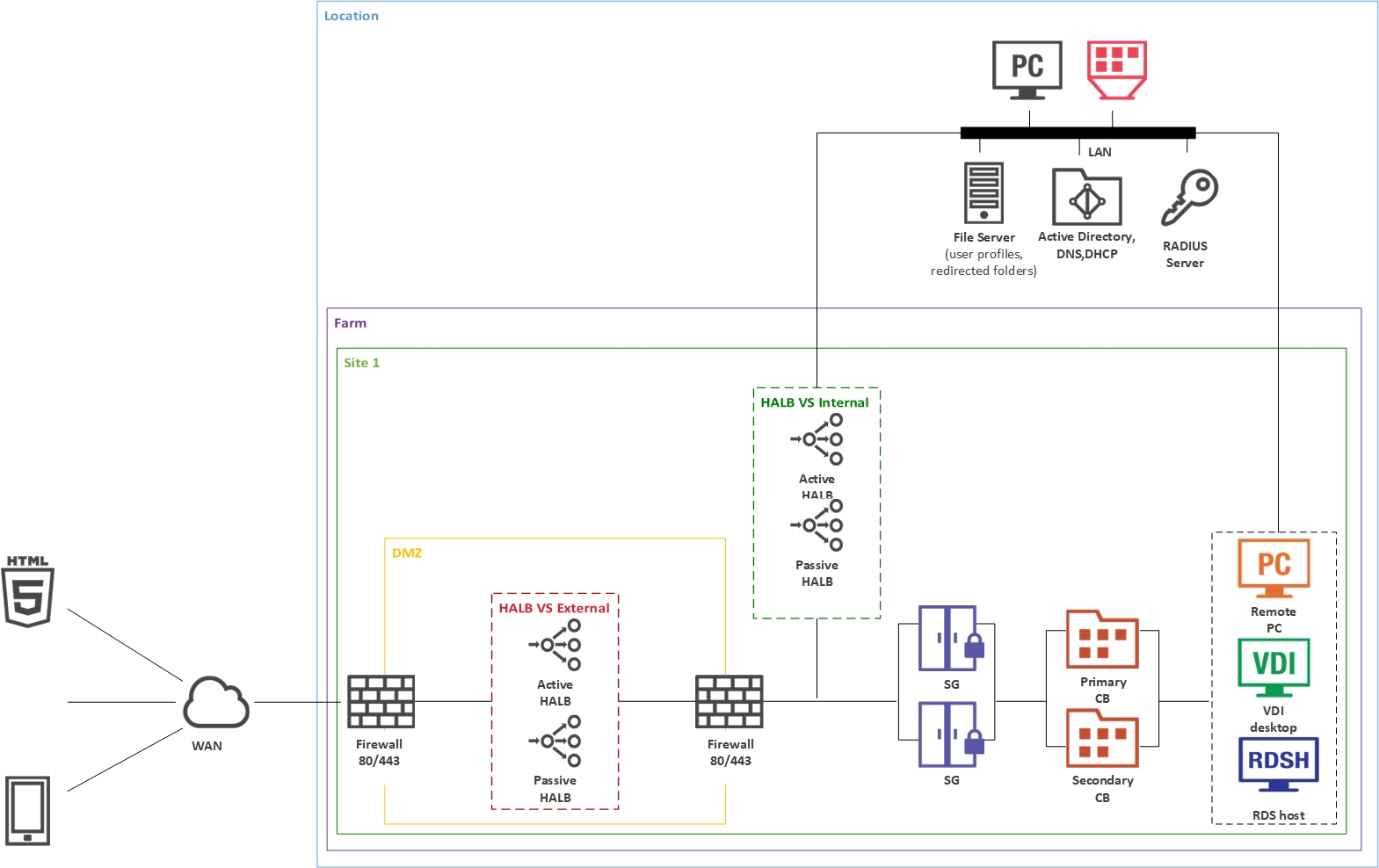
To differentiate traffic between internal and external network, you can use public and private Secure Gateways (both are equal from the RAS perspective):
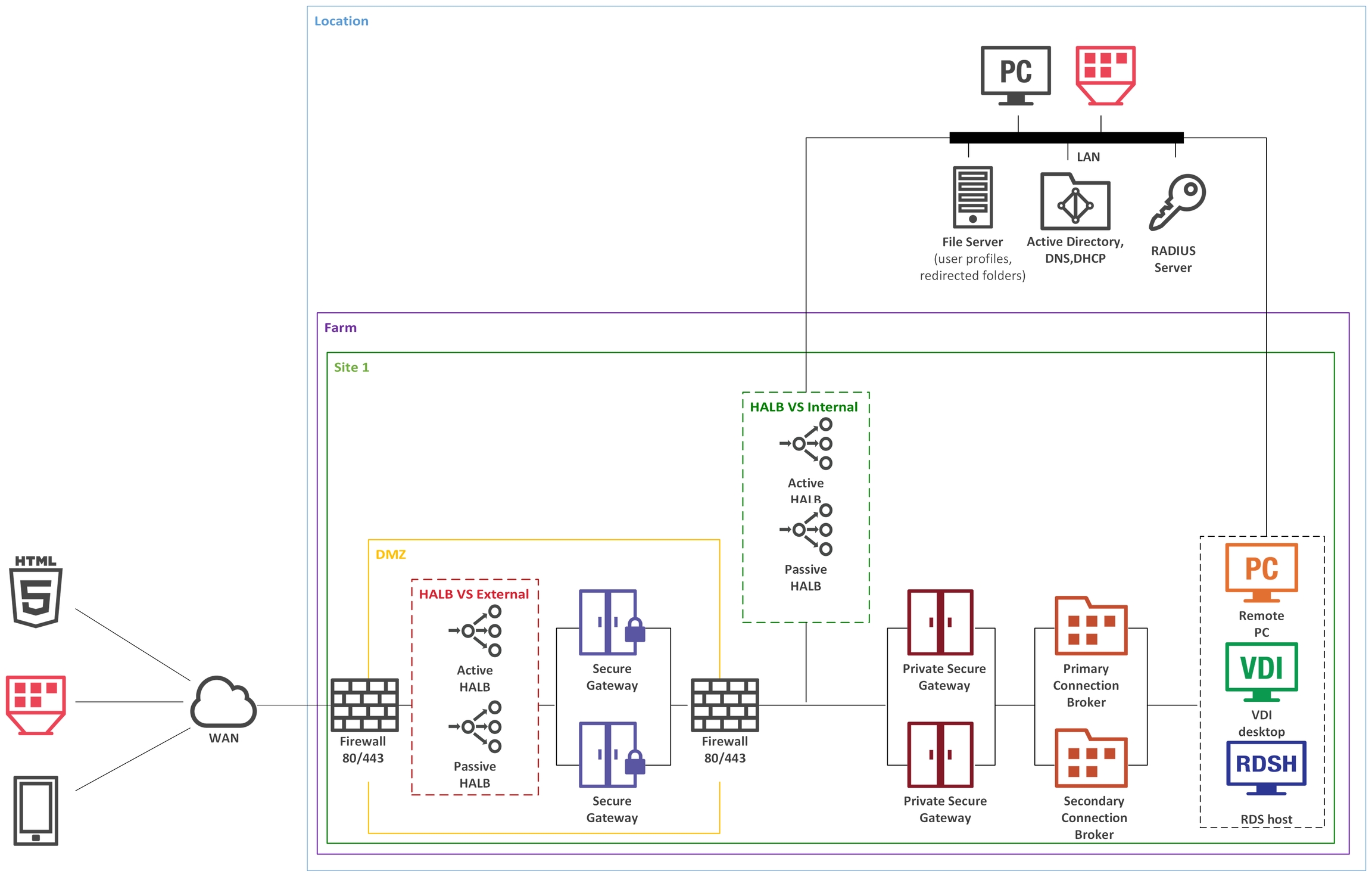
In a configuration of this type, HALB appliances installed in front of RAS Secure Gateways in the internal perimeter network (DMZ). The WAN users connect to the IP address of external HALBS VS, while LAN users use IP address of the internal HALB VS, which use HALB appliances installed in front of the Secure Gateways located in internal network. The Parallels Client settings can be configured either centrally (via Client Policy in the Parallels RAS console) or locally on a device where Parallels Client is running. To add high availability for HALB VS, the second appliance can be deployed for external internal and HALB VS.
Installation Notes
RAS Connection Broker is installed using the Parallels RAS installer (standard installation).
HALB is installed as a ready-to-use virtual appliance and configured in HALB VS properties.
All other components are push-installed from the RAS console.